How should I configure the network interfaces on my ISA Server?
A high-level overview of NIC configuration best practice is provided below:
- The network card name used within the operating system should be changed to closely match the associated ISA Server network name. This clarifies assignment and improves supportability.
- Only one network interface should be configured with a default gateway.
- Only one network interface should be defined with DNS servers.
- Unused or unnecessary bindings should be removed from all interface, where possible, to improve security. This is often termed ‘interface hardening’.
- The default bind order should be amended to define a specific customised order.
Based upon these best practices, the configuration shown below is the standard approach that I normally use as part of my usual ISA Server build process.
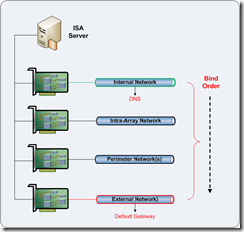
Multiple NIC Deployment - ISA Server Standard Edition
Rename NICs:
Rename all NICs to descriptive names that ideally match the ISA Server network names.
Internal Network
Anonymous Access Perimeter Network
Authenticated Access Perimeter Network
External Network
Etc.
By matching the names, this makes mapping networks between ISA Server and Windows much easier when troubleshooting…
Configure NICs:
Configure NICs:
Internal Network
1. Default Gateway should not be defined
2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
Perimeter Network(s)
1. Default Gateway should not be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Disabled
6. NetBIOS over TCP/IP – Disabled
7. Show icon in notification area when connected – Enabled
External Network 1. Default Gateway should not be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Disabled
6. NetBIOS over TCP/IP – Disabled
7. Show icon in notification area when connected – Enabled
1. Default Gateway should be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Disabled
6. NetBIOS over TCP/IP – Disabled
7. Show icon in notification area when connected - Enabled
Please Note: Disabling the 'File and Print Sharing for Microsoft Networks' binding on the ISA Server internal interface will prevent you from connecting to shares on the ISA Server computer, irrespective of ISA Server system policy or other custom rules that may allow it. This approach is recommended for better security, as your firewall should not beaccessible as a file server!
Amend Bind Order:
Edit the bind order as follows:
Internal Network (Highest)
Perimeter Network(s)
…Others…
External Network (Lowest)
Perimeter Network(s)
…Others…
External Network (Lowest)
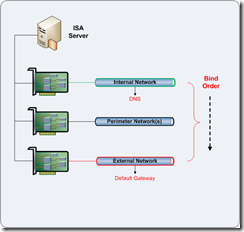
Multiple NIC Deployment - ISA Server Enterprise Edition
With ISA Server Enterprise Edition, it is recommended to add a dedicated Intra-Array NIC. Therefore, we need to consider this additional interface in our configuration.
Rename all NICs to descriptive names that ideally match the ISA Server network names.
Internal Network
Intra-Array Network
Anonymous Access Perimeter Network
Authenticated Access Perimeter Network
External Network
Etc.
Intra-Array Network
Anonymous Access Perimeter Network
Authenticated Access Perimeter Network
External Network
Etc.
Configure NICs:
Internal Network
1. Default Gateway should not be defined
2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
Intra-Array Network
1. Default Gateway should not be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Enabled
5. Client for Microsoft Networks – Enabled NetBIOS over TCP/IP – Enabled
6. Show icon in notification area when connected – Enabled
Perimeter Network(s) 1. Default Gateway should not be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Enabled
5. Client for Microsoft Networks – Enabled NetBIOS over TCP/IP – Enabled
6. Show icon in notification area when connected – Enabled
1. Default Gateway should not be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Disabled
6. NetBIOS over TCP/IP – Disabled
7. Show icon in notification area when connected – Enabled
External Network
1. Default Gateway should be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Disabled
6. NetBIOS over TCP/IP – Disabled
7. Show icon in notification area when connected – Enabled
Amend Bind Order: 1. Default Gateway should be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Disabled
6. NetBIOS over TCP/IP – Disabled
7. Show icon in notification area when connected – Enabled
Edit the network bind order as follows:
Internal Network (Highest)
Intra-Array Network
Perimeter Network(s)
…Others…
External Network (Lowest)
Intra-Array Network
Perimeter Network(s)
…Others…
External Network (Lowest)
Single NIC Deployment – ISA Server Standard Edition
For a single NIC deployment, the following actions are recommended.
Rename NICs:
Rename all NICs to descriptive names that ideally match the ISA Server network names.
Internal Network
By matching the names, this makes mapping networks between ISA Server and Windows much easier when troubleshooting…
Configure NICs:
Internal Network
1. Default Gateway should be defined
2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
Please Note: Disabling the 'File and Print Sharing for Microsoft Networks' binding on the ISA Server internal interface will prevent you from connecting to shares on the ISA Server computer, irrespective of ISA Server system policy or other custom rules that may allow it. This approach is recommended for better security, as your firewall should not beaccessible as a file server!
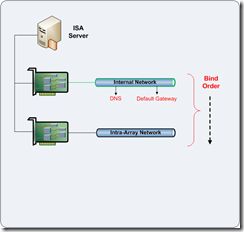
Single NIC Deployment – ISA Server Enterprise Edition
For a single NIC deployment, the following actions are recommended.
Rename NICs:
Rename all NICs to descriptive names that ideally match the ISA Server network names.
Internal Network
Intra-Array Network
By matching the names, this makes mapping networks between ISA Server and Windows much easier when troubleshooting…
Configure NICs:
Internal Network
1. Default Gateway should be defined
2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
Intra-Array Network 2. DNS Servers should be defined
3. Register this connection’s address in DNS – Enabled
4. File and Print Sharing for Microsoft Networks – Disabled
5. Client for Microsoft Networks – Enabled
6. NetBIOS over TCP/IP – Enabled
7. Show icon in notification area when connected – Enabled
1. Default Gateway should not be defined
2. DNS Servers should not be defined
3. Register this connection’s address in DNS – Disabled
4. File and Print Sharing for Microsoft Networks – Enabled
5. Client for Microsoft Networks – Enabled NetBIOS over TCP/IP – Enabled
6. Show icon in notification area when connected – Enabled
Please Note: Disabling the 'File and Print Sharing for Microsoft Networks' binding on the ISA Server internal interface will prevent you from connecting to shares on the ISA Server computer, irrespective of ISA Server system policy or other custom rules that may allow it. This approach is recommended for better security, as your firewall should not beaccessible as a file server!
Amend Bind Order:
Edit the network bind order as follows:
Edit the network bind order as follows:
Internal Network (Highest)
Intra-Array Network
Intra-Array Network
I hope this helps!